The history of computer viruses is a tale of rapid evolution, adaptation, and increasing complexity. Just like biological viruses mutate to survive and evade immunity, computer viruses have transformed over time—constantly changing form and function to outsmart antivirus defenses. From the humble beginnings of boot sector viruses to today’s elusive polymorphic and metamorphic viruses, the journey of digital threats reflects the ongoing arms race between attackers and defenders in cyberspace.
In the earliest stages, viruses were straightforward in design. The most common type in the 1980s was the boot sector virus. These viruses infected the boot sector of a floppy disk or hard drive, ensuring that when a computer was started (booted), the virus would load into memory before the operating system did. One of the most well-known examples was the Brain virus from 1986, which infected the boot sectors of MS-DOS systems and spread via floppy disks. These viruses were effective because users frequently exchanged floppy disks, unknowingly transferring infections from one machine to another.
As the digital ecosystem matured and user behavior changed, so did viruses. By the 1990s, file-infecting viruses became prominent. These viruses attached themselves to executable files such as .exe or .com. When the infected file was opened, the virus activated, often spreading to other files or performing harmful actions like deleting data or corrupting applications. The Jerusalem virus, for instance, was notorious for infecting executable files and deleting them on specific days like Friday the 13th.
But cybercriminals quickly realized a major limitation: these viruses could be detected easily. Early antivirus programs relied on signature-based detection, which meant they scanned files for known patterns of code associated with specific viruses. Once a signature was identified, antivirus software could neutralize the threat. This led virus creators to develop more sophisticated methods of evasion.
Enter polymorphic viruses—a game-changing development in malware history. A polymorphic virus is capable of modifying its code slightly every time it replicates, without altering its core function. This means that every time it infects a new file or system, it looks different, making signature-based detection difficult. Think of it as a virus that wears a different disguise every time it shows up. One famous polymorphic virus was Tequila, which first appeared in the early 1990s. It changed its appearance with each infection but remained functionally identical.
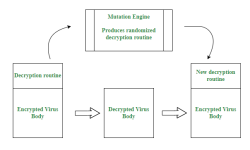
Polymorphic viruses were followed by an even more advanced category: metamorphic viruses. Unlike polymorphic viruses that only encrypt or scramble part of their code, metamorphic viruses can rewrite their entire code structure with each infection. This makes them extremely hard to detect, as there are no reusable patterns. These viruses use mutation engines and even alter the order of operations within their code while maintaining the same effect. They are among the most sophisticated malware types in existence.
In addition to these, virus developers also created stealth viruses, which hide their presence by intercepting system calls and showing uninfected versions of files or sectors when antivirus programs try to scan them. There were also macro viruses, which infected documents like Microsoft Word files by exploiting built-in scripting features. These became especially popular in the late 1990s as email usage surged.
What drives this constant mutation? In simple terms: survival. As antivirus solutions become smarter and more proactive, virus creators have to innovate to remain effective. This cat-and-mouse game between malware authors and cybersecurity professionals continues to fuel virus evolution.
Interestingly, this trend is not only technical but psychological. Today’s malware often includes social engineering components—tricks that manipulate users into clicking malicious links, downloading infected files, or sharing confidential information. So while code complexity increases, virus creators are also investing in deception and human error as infection vectors.
In conclusion, the mutation of computer viruses from simple boot sector infections to shape-shifting polymorphic threats illustrates the dynamic nature of cybersecurity. As long as technology continues to evolve, so will the strategies used to exploit it. Staying updated, using layered security, and practicing safe computing habits are essential in an age where viruses are no longer predictable lines of code—but evolving digital organisms built to survive.
Did you know that some modern viruses can change their entire code each time they infect a system? Have you ever experienced a virus infection on your device? Share your stories or questions below—let’s discuss how viruses have adapted and what we can do to stay one step ahead.
In the earliest stages, viruses were straightforward in design. The most common type in the 1980s was the boot sector virus. These viruses infected the boot sector of a floppy disk or hard drive, ensuring that when a computer was started (booted), the virus would load into memory before the operating system did. One of the most well-known examples was the Brain virus from 1986, which infected the boot sectors of MS-DOS systems and spread via floppy disks. These viruses were effective because users frequently exchanged floppy disks, unknowingly transferring infections from one machine to another.
As the digital ecosystem matured and user behavior changed, so did viruses. By the 1990s, file-infecting viruses became prominent. These viruses attached themselves to executable files such as .exe or .com. When the infected file was opened, the virus activated, often spreading to other files or performing harmful actions like deleting data or corrupting applications. The Jerusalem virus, for instance, was notorious for infecting executable files and deleting them on specific days like Friday the 13th.
But cybercriminals quickly realized a major limitation: these viruses could be detected easily. Early antivirus programs relied on signature-based detection, which meant they scanned files for known patterns of code associated with specific viruses. Once a signature was identified, antivirus software could neutralize the threat. This led virus creators to develop more sophisticated methods of evasion.
Enter polymorphic viruses—a game-changing development in malware history. A polymorphic virus is capable of modifying its code slightly every time it replicates, without altering its core function. This means that every time it infects a new file or system, it looks different, making signature-based detection difficult. Think of it as a virus that wears a different disguise every time it shows up. One famous polymorphic virus was Tequila, which first appeared in the early 1990s. It changed its appearance with each infection but remained functionally identical.
Polymorphic viruses were followed by an even more advanced category: metamorphic viruses. Unlike polymorphic viruses that only encrypt or scramble part of their code, metamorphic viruses can rewrite their entire code structure with each infection. This makes them extremely hard to detect, as there are no reusable patterns. These viruses use mutation engines and even alter the order of operations within their code while maintaining the same effect. They are among the most sophisticated malware types in existence.
In addition to these, virus developers also created stealth viruses, which hide their presence by intercepting system calls and showing uninfected versions of files or sectors when antivirus programs try to scan them. There were also macro viruses, which infected documents like Microsoft Word files by exploiting built-in scripting features. These became especially popular in the late 1990s as email usage surged.
What drives this constant mutation? In simple terms: survival. As antivirus solutions become smarter and more proactive, virus creators have to innovate to remain effective. This cat-and-mouse game between malware authors and cybersecurity professionals continues to fuel virus evolution.
Interestingly, this trend is not only technical but psychological. Today’s malware often includes social engineering components—tricks that manipulate users into clicking malicious links, downloading infected files, or sharing confidential information. So while code complexity increases, virus creators are also investing in deception and human error as infection vectors.
In conclusion, the mutation of computer viruses from simple boot sector infections to shape-shifting polymorphic threats illustrates the dynamic nature of cybersecurity. As long as technology continues to evolve, so will the strategies used to exploit it. Staying updated, using layered security, and practicing safe computing habits are essential in an age where viruses are no longer predictable lines of code—but evolving digital organisms built to survive.
Join the Conversation:
Did you know that some modern viruses can change their entire code each time they infect a system? Have you ever experienced a virus infection on your device? Share your stories or questions below—let’s discuss how viruses have adapted and what we can do to stay one step ahead.